The NetBIOS protocol contains a vulnerability that allows a Windows VPS which has this service enabled to be used in an amplification DDoS attack.
In this article we'll explain the risk of the vulnerability in the NetBIOS service, and show how you can secure your VPS against abuse of the NetBIOS service.
The NetBIOS vulnerability
NetBIOS is a data communication protocol with which external systems/applications can communicate over a local network. For example, it was used to gain remote access to shared folders on an internal network.
The NetBIOS service is now out of date and is hardly used anymore. If the NetBIOS service is still enabled and is publicly accessible, NetBIOS can be abused in an amplification (D)DoS attack.
Simply put, in an 'amplification attack' an amount of data is sent to your UDP port from a spoofed IP. Your VPS then sends a significantly larger amount of data back to the actual IP. This way, malicious parties can abuse your UDP port to perform a (D)DoS attack on the spoofed IP address.
For this reason, it is not permitted that the NetBIOS service is publicly accessible on a VPS at TransIP.
Preventing NetBIOS abuse
Use the steps below, depending on your OS and firewall, to prevent abuse of the NetBIOS service.
The VPS-Firewall in your control panel
-
Instead of using the firewall of your operating system, you can also use the VPS-Firewall in the control panel. By using the VPS-Firewall in the control panel, all ports are automatically closed and you decide then which ports are opened.
Step 1
Log in to your control panel and navigate to the relevant VPS.
Step 2
Click the cogwheel behind 'Network' (directly under the VPS console) and click 'VPS-Firewall'.
Step 3
Enable the firewall by setting the switch to 'On' behind 'Enable VPS-Firewall for this VPS'. The most commonly used ports are then automatically opened.

Your VPS is now secure! More information about opening ports with the VPS-Firewall can be found in our VPS-firewall documentation.
Closing port 137 in Iptables
-
Stap 1
Connect to your VPS through SSH and close port 137 using the command:
sudo iptables -A INPUT -p tcp --dport 137 -j DROP
sudo iptables -A INPUT -p udp --dport 137 -j DROP
-
Stap 2
Reload your firewall:
iptables-save | sudo tee /etc/sysconfig/iptables
service iptables restart
Closing port 137 in Firewalld (CentOS, Plesk, DirectAdmin, cPanel)
-
Step 1
Connect to your VPS through SSH and close port 137 using the commands (Plesk uses the zone plesk instead of public):
sudo firewall-cmd --zone=public --remove-port=137/tcp
sudo firewall-cmd --zone=public --remove-port=137/udp
-
Step 2
Reload your firewall to process the changes:
sudo firewall-cmd --reload
Closing port 137 in UFW
Connect to your VPS through SSH and close port 137 using the command:
sudo ufw deny 137
Closing port 137 in FreeBSD
Add the following lines to /etc/ipfw.rules:
$cmd 00320 deny tcp from any to any 137 in via $pif
$cmd 00320 deny tcp from any to any 137 in via $pif
Disabling the NetBIOS service
-
NetBIOS uses various services. When you disable the NetBIOS service in Windows under 'Internet Protocol Version 4 (TCP / IPv4)' it will only disable the session service, and still allows for exploits of the NetBIOS service.
As such, don't soly disable the NetBIOS service, but block the port in the firewall, see below.
Closing the NetBIOS port in Windows firewall
-
In addition to turning off the NetBIOS service, you can prevent misuse of the NetBIOS service by closing TCP & UDP port 137 in your Windows firewall. In that case, you do not have to also disable the NetBIOS service.
Step 1
Open Windows Firewall with Advanced Security and click 'Inbound'> 'New Rule'.
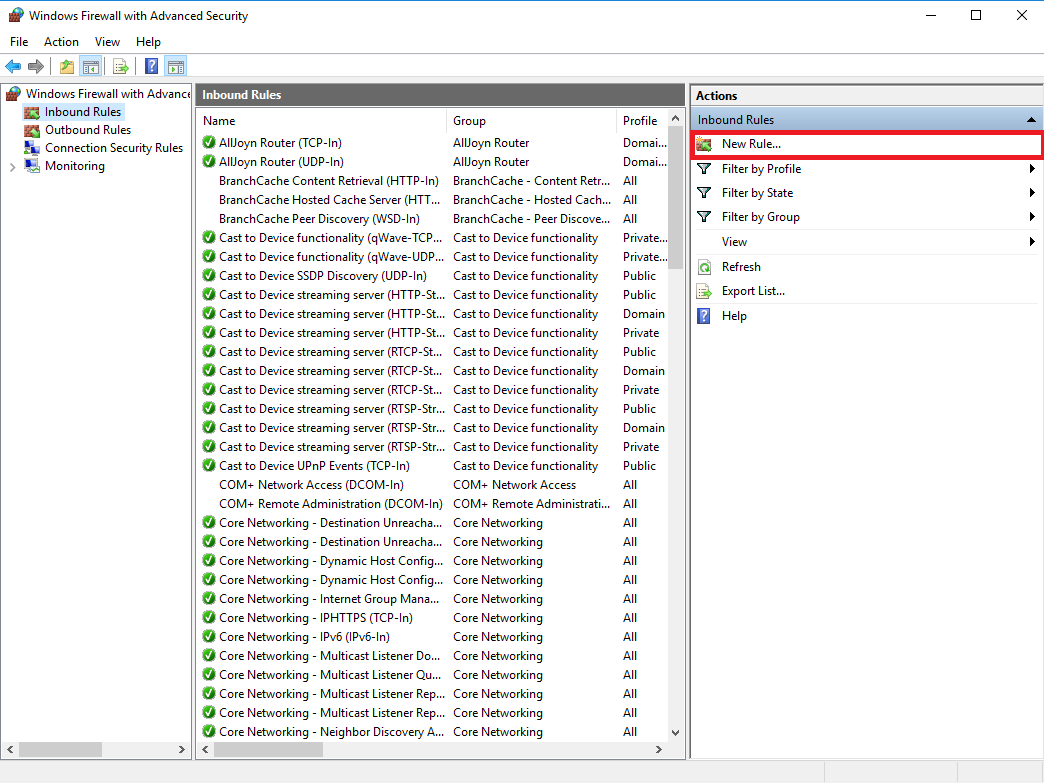
Step 2
Select 'Port' and click 'Next'.
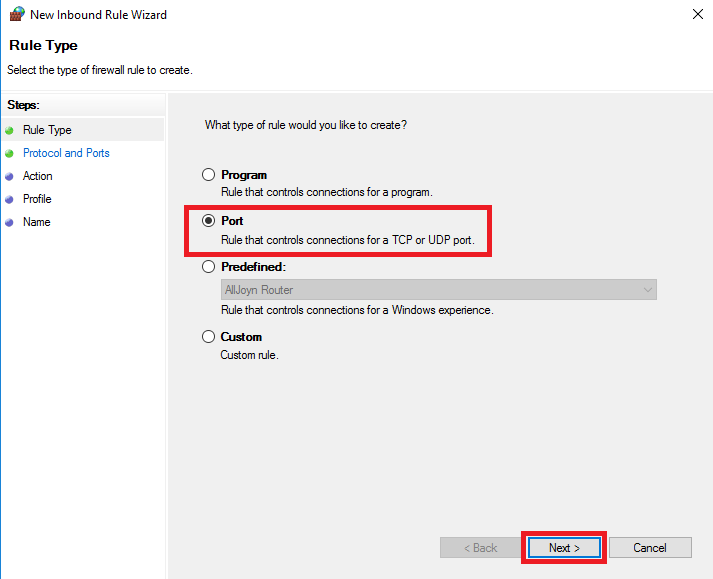
Step 3
Select 'UDP' as the protocol and specify port number 137 specifically.
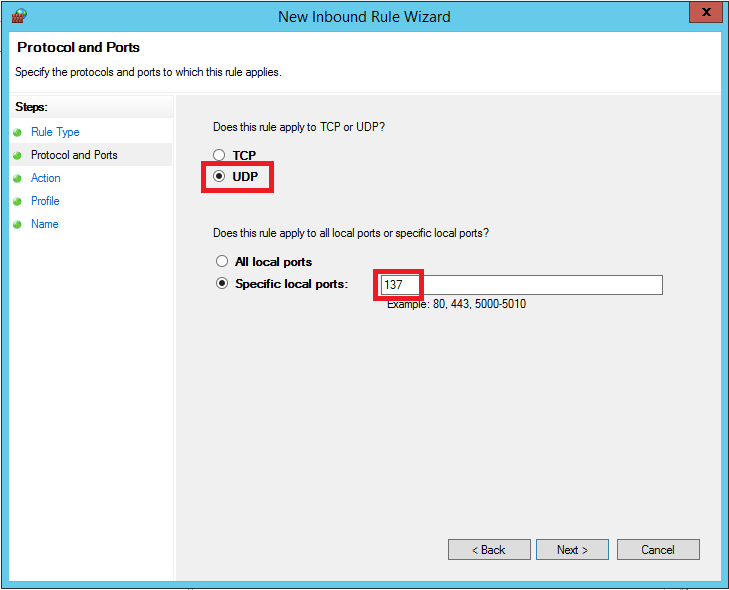
Step 4
You want to prevent abuse of the port, so select 'Block the connection' and click 'Next'.
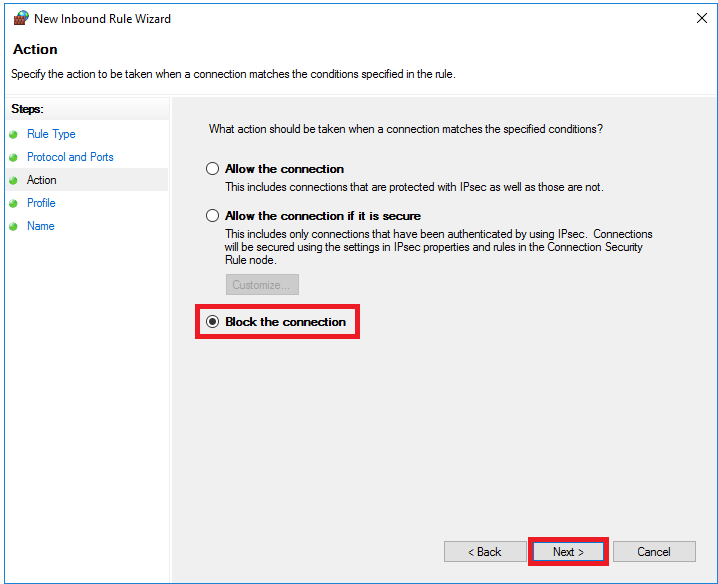
Step 5
The safest option is to apply the blockade to Domain, Private and Public. Leave these options checked and click 'Next'.
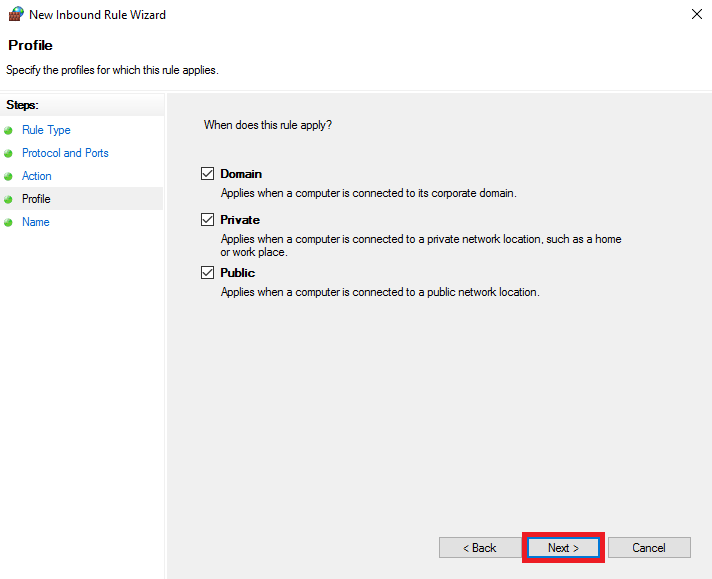
Step 6
Give the rule a clearly recognizable name and click 'Finish'.
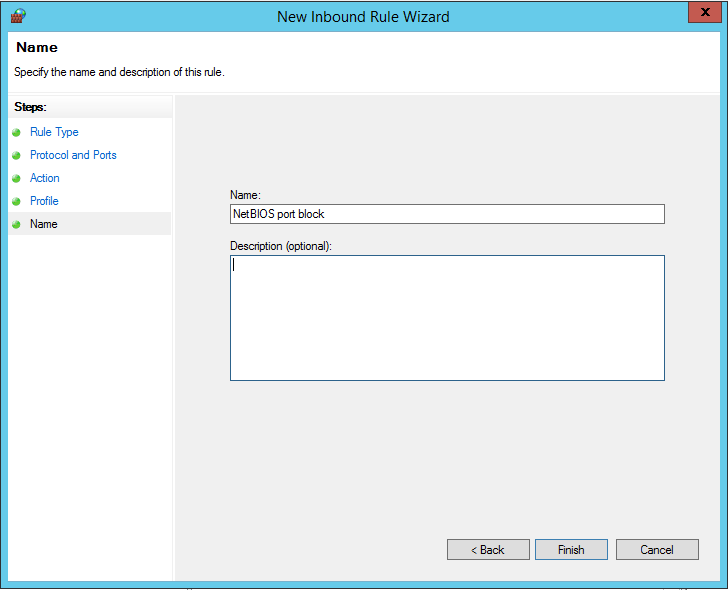
The UDP port used by the NetBIOS service is now blocked and third parties can no longer take advantage of it. Repeat these steps once more, but use TCP at step 3 instead of UDP.
In this article, we have shown how to prevent abuse of the NetBIOS service on your Windows VPS.
Should you have any questions left regarding this article, do not hesitate to contact our support department. You can reach them via the ‘Contact Us’ button at the bottom of this page.











