-
TL;DR: update OpenSSL to 1.1.1g to protect your server against this vulnerability.
- This article only applies to Ubuntu 20.04 (beta), Suse, Debian 10 Buster, Debian Bullseye, Debian Sid, OpenSuse, ArchLinux, CoreOS and Gentoo .
On April 21, 2020, OpenSSL announced the vulnerability of OpenSSL 1.1.1d, 1.1.1e, and 1.1.1f and released a security update for it. As a result of this vulnerability, services using both TLS 1.3 and these OpenSSL versions may be vulnerable to Denial of Service (DoS) attacks.
In this article, we provide more information about this vulnerability and explain how to protect your VPS against it.
The vulnerability
When establishing an SSL connection, a 'handshake' procedure is performed to establish a secure connection between the client and server.
If you use TLS 1.3 in OpenSSL 1.1.1d, 1.1.1e and 1.1.1f, a specific function (SSL_check_chain) can be called during or after this handshake process. If an attacker sends an invalid or empty signature and the SSL_check_chain function is called, a 'NULL pointer dereference' occurs. The SSL_check_chain function then 'breaks', causing the application that uses it to crash.
Check if your VPS is vulnerable
You can easily check your VPS for this OpenSSL vulnerability by checking the version number of OpenSSL. To do this, use the following commands:
openssl version
The output looks like the example below. Is version number 1.1.1d, 1.1.1e, or 1.1.1f shown here? Then your VPS is vulnerable.
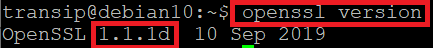
Debian 10 Buster
In Debian Buster stable, you'll always see 1.1.1d as version. For Debian Buster, check if you've installed update 1.1.1d-0+deb10u3 using the command:
apt-cache policy openssl
The output will look as follows. If you don't see version 1.1.1d-0+deb10u3 or newer here, your VPS is vulnerable.
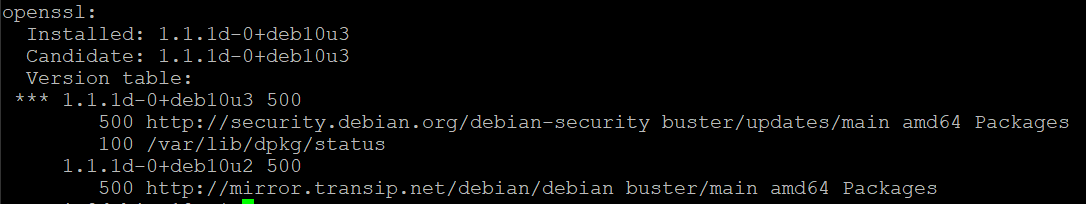
Securing your VPS
Are you using OpenSSL version number 1.1.1d, 1.1.1e or 1.1.1f? Then you just need to update OpenSSL to 1.1.1g to fix the problem. For example, in Debian 10 / Ubuntu 20.04 you do this with the command:
sudo apt -y update && sudo apt -y upgrade
Finally, check whether the update to OpenSSL 1.1.1.g was successful with the command :
openssl version
Or in Debian 10:
apt-cache policy openssl
That's it! Your VPS can now no longer be exploited through this vulnerability in OpenSSL. For more general tips for securing your VPS, see this article.
If you have any questions regarding this article, please do not hesitate to contact our support department. You can reach them via the button 'Contact us' at the bottom of this page.
Do you want to discuss this article with other users? Please leave a message under 'Comments'.




