A severe vulnerability has been found in ProFTPD, widely used FTP server software.The vulnerability is caused by the mod_copy module of ProFTPD.
This vulnerability allows an attacker to copy any file on a ProFTPD server without needing write permissions, or to execute random code remotely. The attacker requires a user account for this, or anonymous access to the ProFTPD server (anonymous access is insecure and we recommend against it).
At the time of writing, no patched version of ProFTPD is available yet. In this article, we explain how you can check for this vulnerability and secure your ProFTPD server.
- TransIP's systems are not susceptible to this vulnerability.
- By default, our DirectAdmin and cPanel installations use PureFTPD and not ProFTPD.
- Plesk uses ProFTPD, but newer versions come without the vulnerable mod_copy module, see this article.
Check whether you are using ProFTPD and whether ProFTPD is vulnerable
There are several ways to check whether you are using ProFTPD and whether the mod_copy module is active. The easiest is with the following command (if you use a different port for FTP than 21, you should use that port number in the command):
.
$ echo -e "FEAT\nQUIT\n" | nc localhost 21 | grep COPYIf you use ProFTPD and the mod_copy module is active, you will see an output as in the screenshot below.
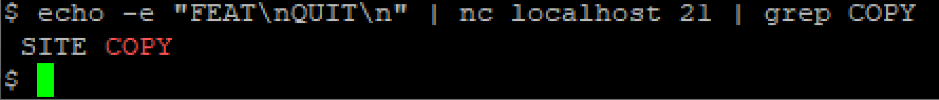
Do you not see "SITE COPY" in the output? Then your VPS is not vulnerable.
Securing your VPS
There are two ways at this time to secure your VPS against misuse of the mod_copy module:
- Disabling the mod_copy module in ProFTPD
- Using another FTP server or SFTP via OpenSSH.
We recommend using a different FTP program or OpenSSH instead of ProFTPD. ProFTPD is less actively maintained than other alternatives such as PureFTP and vsftpd.
Disabling mod_copy
Step 1
Open the ProFTPD configuration. You use one of the following commands depending on your operating system:
CentOS
sudo nano /etc/proftpd.confUbuntu / Debian
sudo nano /etc/proftpd/modules.conf
Step 2
Place a # in front of the line in which the mod_copy module is loaded. The result is as follows:
# Save the changes and close the file (ctrl + x > y > enter).
Step 3
Finally, restart ProFTPD to process the changes:
systemctl restart proftpdFor Plesk, use the command:
systemctl restart xinetd
Using another FTP program or SFTP via OpenSSH
Instead of modifying the ProFTPD configuration, you can also use another FTP program or SFTP via OpenSSH. You can use our manuals, which can be found on the following pages:
FTP via vsftpd
SFTP via OpenSSH
If you use one of these options, do not forget to remove or disable ProFTPD on your VPS as follows:
Disable ProFTPD:
sudo systemctl stop proftpd
sudo systemctl disable proftpdRemove ProFTPD:
Ubuntu / Debian:
sudo apt -y remove proftpd-basicCentOS:
sudo yum -y remove proftpd
You're now no longer vulnerable for ProFTPD's mod_copy vulnerability! Should you have any questions left regarding this article, do not hesitate to contact our support department. You can reach them via the ‘Contact Us’ button at the bottom of this page.




