Spammers often try to impersonate third-party domains by spoofing them. The more well-known and trusted the party they impersonate, the greater the chance that a recipient will read the spam.
In addition to the necessary measures such as SPF control, you can use DKIM. DKIM is used to check the validity of the email sender. When sending emails, a digital signature is sent with DKIM. This is checked using the key that is included in the DKIM record.
In this tutorial, we show you how to sign outgoing mail with DKIM on a VPS with CentOS 7 and Exim. Incoming mail can be automatically scanned for DKIM with Spamassassin.
- The steps in this article require a CentOS 7 or 8 VPS with Exim and Dovecot. In this tutorial, we explain how to set up Exim and Dovecot.
- Execute the commands in this article using sudo, or as a root user
Step 1
Connect to your VPS via SSH or the VPS console in the TransIP control panel.
Step 2
Go to the Exim directory and then generate a private and public key for signing your mail:
cd /etc/exim
openssl genrsa -out dkim.private.keyYou are free to change the directory /etc/exim and the name dkim.key. Please note that you use the same directory and name in the following steps as well.
Next, you extract the public key from the .key file that you just created with the command:
openssl rsa -in dkim.private.key -out dkim.public.key -pubout -outform PEMYou add the public key in the DNS records of the domains that mail through your mail server. We will get back to this in step 7.
Step 4
DKIM support is available in Exim in CentOS 7 by default. Therefore, you only need to enable DKIM in the configuration of Exim. Open the Exim configuration, for example with:
nano /etc/exim/exim.conf
Step 5
Under 'Transports Configuration', search for the part:
remote_smtp:
driver = smtpThis transport takes care of sending mail from your VPS to another mail server. Add the following directly below the code above:
dkim_canon = relaxed
dkim_domain =
dkim_private_key = /etc/exim/dkim.private.key
dkim_selector = keyThe entire remote_smtp transport can then look like this:
remote_smtp:
driver = smtp
message_size_limit = ${if > {$max_received_linelength}{998} {1}{0}}
dkim_canon = relaxed
dkim_domain = ${sender_address_domain}
dkim_private_key = /etc/exim/dkim.private.key
dkim_selector = keyThen save the changes and close the file (ctrl + x > y > enter).
Step 6
Finally, restart Exim to process the changes:
systemctl restart eximFor every domain with which you send mail from your VPS, you need a TXT record in which the public key is included. In step 3, you created a separate .key file containing your public key. Print the contents of this file with the command:
cat /etc/exim/dkim.public.keyThe output looks like this:
-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQBAA4GNADCBiQKBgQDU4Fi7KotzLl789XQtY7nGU7Pd
sJ7tz1cTrr5JL6NNNO2bICv8rmm6fslxtk0nH0tvomsHY4d7A9IoCVog7QMs67Px
YXubn0sT2Ye5VtxkgHj6yaMpwUCMzQE1TzyLdnn6fYveRrTHBAeeGVE33svW/d1h
n11NKwcRxGtXveqc2QIDAQAB
-----END PUBLIC KEY-----Copy the content in a text editor (for example, notepad or TextEditor), delete the first and last line and place the entire content on one line so you get a long code as below:
You then create a TXT record in the DNS settings of each domain for which you send mail on your VPS using the syntax below.
- name:_domainkey
- ttl: 5 min
- type: TXT
- value: v=DKIM1; k=rsa; p=MIGfMA0GCSqGSIb3DQEBAADCBiQKBgQDU4etcetera
- Replace the value after p= with the value of your public key that you noted in step 7.
- Do you mail from a subdomain? Then, the name of your DNS record will be key._domainkey.yoursubdomain.
In the TransIP control panel, for example, the result looks like this:
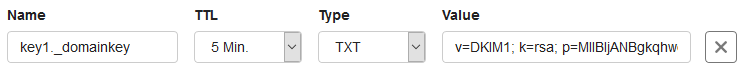
Finally, save your new record. It then takes a maximum of 24 hours (usually no longer than an hour) for the changes to be processed. This is due to the worldwide processing time of DNS changes and unfortunately, we have no influence on it.
Renewing public and private keys
In this manual, you have generated a public and private key with OpenSSL. SSL keys do not expire (as opposed to SSL certificates), but for security reasons, it is advisable to replace your public and private keys from time to time (for example annually).
A relatively simple way to achieve this is through a construction with multiple DKIM records. We also use such a construction for TransIP, and this works as follows:
Earlier in this article, we explained that the DKIM selector is the first part of the DKIM record name. The selector 'key' therefore gives you the subdomain name 'key._domainkey'. Suppose you want to mail on behalf of example.com, and the domain that you use as SMTP/MX domain is mymailserver.com.
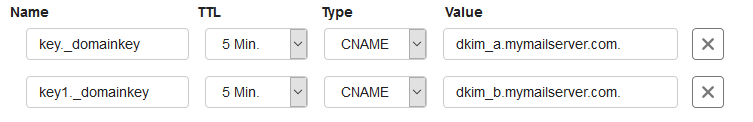
Instead of creating a TXT record named 'key._domainkey', create two CNAME records in the DNS settings of each domain that sends mail via your VPS (here example.com), for example, the following:
- For the DKIM check, this example looks at the value of key._domainkey.example.com. This is because the dkim_selector is set to 'key'. key1._domainkey.example.com is not currently being used.
- _domainkey.example.com refers to the dkim_a. mymailserver.com subdomain. In the DNS settings of mymailserver.com, you actually create the TXT record for the dkim_a subdomain in which your public key is included, so for example:
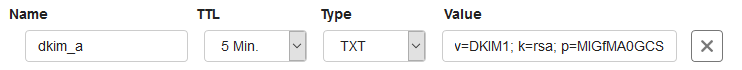
- You don't have to create a record for dkim_b. mymailserver.com at the moment (key1._domainkey refers to it). You only do this when you want to update your keys.
Now imagine that you want to update your public and private key. You then generate a new key (see step 2), but then for the dkim_b record, for example:
cd /etc/exim
openssl genrsa -out dkim_b.private.key
openssl rsa -in dkim_b.private.key -out dkim_b.public.key -pubout -outform PEMYou then create a TXT record for dkim_b (see steps 7 and 8) for your SMTP domain (here mymailserver.com) using the public key that you have just created. After creating this record, wait 24 hours before proceeding so the DNS change has had time to propagate.
Now, adjust the value of the private_key and dkim_selector in the Exim configuration (/etc/exim/exim.conf) so that those of key1 / dkim_b are used, for example:
dkim_private_key = /etc/exim/dkim_b.private.key
dkim_selector = key1Then restart Exim. From that moment on, the public and private key that start with the name dkim_b are used and for example.com of the key1._domainkey DNS record, which in turn refers to dkim_b.mymailserver.com.
Repeat these steps to generate new keys for dkim.private.key and dkim.public.key, adjust the TXT record of dkim_a.mymailserver.com to the new public key and then reset the dkim_selector to the 'key' value.
This brings us to the end of this manual about the use of DKIM in Exim. Should you have any questions left regarding this article, do not hesitate to contact our support department. You can reach them via the ‘Contact Us’ button at the bottom of this page.




